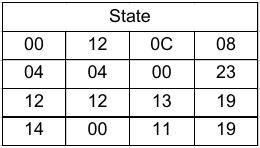
AES is based on the substitution-permutation network principle and is similar to Rijndael cipher. It’s block length is fixed to be 128 bits and key length can vary like 128, 192 or 256 bits where the encryption requires 10, 12 and 14 rounds respectively to get the cipher text. In this every input and output of an operation is termed as a state which is an array of 4X4 bytes.
Eg. Plain Text : AES USES A MATRIX ZZ
Hexadecimal : 00 04 12 14 12 04 12 00 0C 00 13 11 08 23 19 19
AES encryption involves four transformations which transforms the state given as the input to a different state. The four transformations are:
- Sub Bytes
- Shift Rows
- Mix Columns
- Add Round key
Sub Bytes Transformation
The values in the state is substituted by another values according to a lookup table called S-box.
Shift Rows Transformation
ShiftRows method operates on the rows of the state, the nth row is shifted left circular by n-1 bytes.
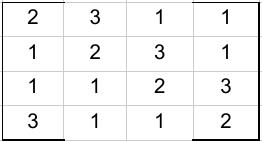
Mix Columns Transformation
In this step four bytes of each column is replaced by doing multiplication with a fixed matrix shown below,
Matrix multiplication with hexadecimal is a combination of multiplication and addition similar to the normal matrix multiplication. The multiplication part follow the following mentioned rules:
Multiplication with 1: No change in the value
Multiplication with 2: Left shift with no carry. In addition to that XOR with 0X1B if the shifted bit is 1.
Multiplication with 3: Perform multiplication with 2 then XOR with the initial value.
While the addition part is simply XOR.
Add Round key Transformation
Here each byte of the input state is combined with corresponding byte of the subkey by doing bitwise XOR. The subkey for each round is generated by Rijndael’s key expansion method.
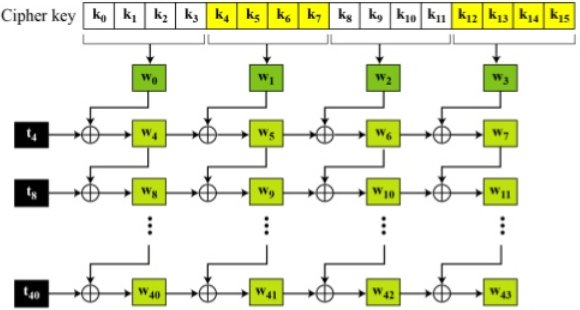
Key expansion in AES
Key expansion is done using three operations described below:
- Rotate : A 32 bit word is rotated eight bits to the left.
- 08 23 19 0C => 23 19 0C 08
- S-box :
The value is replaced by using the lookup table given above as follows :
- C3 => 2E
- Rcon : The value is XORed with the round constant depending on the round number.
Key used for encryption is of 128 bits arranged as four words,
 (i) If i is not a multiple of 4, wi is formed as,
(i) If i is not a multiple of 4, wi is formed as,
wi = wi-1 ⊕ wi-4
(ii) If i is a multiple of 4, wi is formed as,
wi = temp ⊕ wi-4
temp is a 32 bit word formed from wi-1 in the following manner :
wi-1 => Left shift 8 bits => S-Box => ⊕ Rconi/4 => tempi
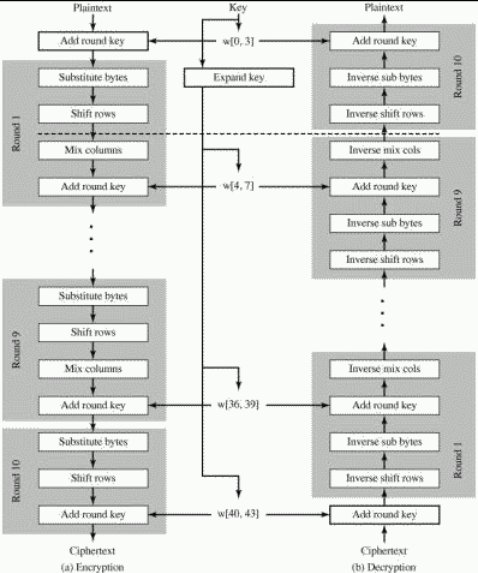
Now, the AES encryption can be done in 11 rounds, where the initial round, Round 0 involves an Add Round Key transformation with the initial key comprising of w0, w1, w2 and w3. Following 9 rounds comprises of Sub Bytes, Shift Rows, Mix Columns followed by Add Round key with the subkey generated for that round. The final round involves all the above rounds except Mix Columns. After that the cipher text is ready.